
With the exponential rise of quantum computing in recent years, current encryption algorithms used to secure our data and communications networks are at risk of becoming obsolete. Using the Shor algorithm, the power of a quantum computer will be able to break modern encryption standards sparking the largest cryptographic migration in the history of computing – requiring organizations to replace legacy encryption with quantum-safe cryptography.
For more than four decades the industry has relied on public-key encryption where both key generation and key distribution processes were embedded at the endpoint. This makes it very hard to change the encryption infrastructure at all, because some endpoints may not support new algorithms/technologies, let alone scale. Pulling encryption, key generation, distribution, and management from the data plane and into a control plane is a way to get faster adoption, more seamless integration, and the agility to adapt to new encryption algorithms/technologies easily and at scale. However, those same organizations should ensure they are quantum-safe now, not tomorrow or the day after, as they otherwise risk premature obsolescence – a scenario best avoided.
Some of the Current Challenges
The Alice and Bob Problem
One of the recurring challenges with current cryptography is to safely deliver a symmetric encryption key between two parties over an unsecure network like the Internet. With Public Key Encryption (PKE), encryption keys used to encrypt information to protect it while at rest or in transit, are generated on the endpoint and travel together over the same, unsecure communication channel (e.g., Internet) as the data; if intercepted by malicious actors, they could be used to decrypt all communications between these parties.
Mobile Devices
This gets even more difficult when dealing with mobile endpoints like smartphones or tablets, connecting over different networks throughout the day (e.g., cellular, private and/or public Wi-Fi), constantly changing their IP address.
“Harvest Now, Decrypt Later” Attack
Even though many organizations might think their data is still somehow secure against today's attacks, a malicious actor could still manage to intercept their communications and collect that data to decrypt it later using a quantum computer. This is a very real scenario wherein half of all organizations are believed to be at risk!
Insufficient, Platform-Dependent Entropy
Endpoint-generated keys are based on the available entropy of the local platform, which means that similar IoT devices, cloud computing instances, or mobile devices tend to generate keys similar to their peers. An attacker can generate keys using the same platform to try to create duplicates, or worse, determine a pattern in the key generation process that would let them predict keys.
Current Solutions and Their Limitations
Solving these issues requires a paradigm shift, where the encryption keys are no longer sent over the same, unsecure channel/path as the data they are used to protect, but separately over a managed, quantum-secure network. There are currently several approaches to post-quantum security from industry to protect communications from post-quantum attacks.
Post-Quantum Cryptography (PQC)
Post-Quantum cryptography (PQC) refers to using new cryptographic algorithms thought to be secure against a cyberattack from a quantum computer, to encrypt data and protect it while travelling over unsecure networks like the Internet. Standardization efforts are currently underway by the National Institute of Standards and Technology (NIST), though approved commercial implementations of forthcoming standards are still several years away.
Quantum Key Delivery (QKD)
Quantum Key Delivery (QKD) solutions use photons sent over a dedicated fiber link to generate identical encryption keys at both ends of the connection. Due to the properties of quantum physics, these photons cannot be observed nor intercepted without changing their state, ensuring said keys cannot be stolen nor tampered with, thus preventing any possibility of a Man-In-The-Middle (MITM) attack. This technology requires dedicated hardware appliances, connected point-to-point using optical fiber connections, with a maximum secure range of 100 km.
Quantum Random Number Generator (QRNG)
Quantum Random Number Generator (QRNG) relies on randomness of quantum mechanics, by nature non-deterministic, to generate/produce true random numbers (called “quantum entropy”). QRNG has been in use for several years already, for example, by online casinos for their gaming and gambling services where randomness is key (e.g., slot machines). It requires specific hardware (chipset).
So far, all these approaches were mutually exclusive, and not easy to integrate for any organization as they would require changing/adapting the current cryptography protocols used in the whole organization; also, the endpoints (desktop or laptop computer, mobile devices, etc.) are directly involved, which translates into a huge effort as well as an impact/downtime for the employees.
What Is Phio Trusted Xchange™?
Phio Trusted Xchange™ (TX) is a quantum-safe and crypto-agile enterprise management platform that represents a paradigm shift in cryptography, enabling enterprises to implement effective cryptographic policy to stay ahead of the evolving threat landscape, advances in computing, and everyday cybersecurity risks.
Its secure key delivery capabilities include scalability, continual key rotation, fault tolerance, load balancing and diverse routing. It is designed to separate the symmetric encryption key delivery from the data channel for greater agility, flexibility, and control. It securely transmits encryption keys over any medium that supports IPv4 or IPv6 i.e., fiber, optical, satellite, 4G/5G, copper) and delivers them out-of-band to line encryptors or any system that can accept symmetric encryption keys.
Phio TX platform also provides visibility into what is currently an opaque encryption ecosystem that will only get more complex as the quantum era nears and organizations begin to replace legacy encryption with quantum-resistant cryptography. The auditable, crypto control plane allows you to see how often keys are rotated, which parties are exchanging keys and of what strength, and what technologies are being used to protect keys across the network. It also simplifies the creation of ad-hoc key exchanges with third parties without requiring direct access to your network from the clients.
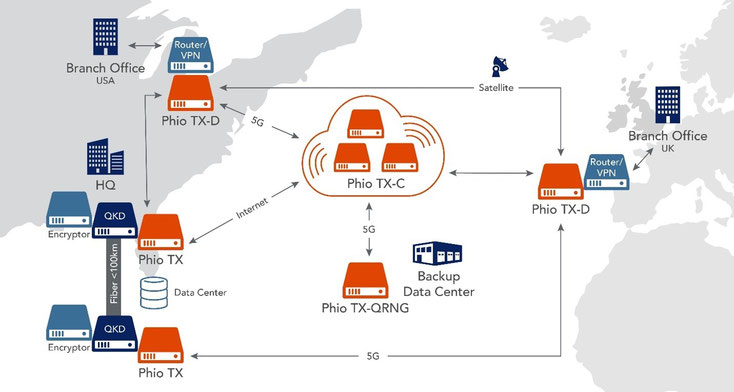
How Does Phio TX Help with Current Challenges?
In the case of the “Alice and Bob problem,” Phio TX helps with securely delivering a key, initially requested by Alice to Bob, ensuring it cannot intercept nor be tampered with at any point during its transit.
Practical Example
An application, called client A (e.g., VPN client on a mobile device), needs a new encryption key to communicate with a backend system, called client B (e.g., VPN access point), to establish a secure, end-to-end communication channel (e.g., VPN tunnel) between them.
- Each encryption client is assigned to one or more Phio TX nodes.
- When Client A makes a request for the key(s) it also specifies its counterpart, Client B, which receives the same key(s).
- Phio TX connected to Client A generates the key(s) of specified length then delivers it to the Phio TX node connected to Client B using a dynamic path. Client A receives the same key(s) and ID(s) only if the transaction was successful.
- This ensures that when Client A receives the key, Client B can also receive the same key.
- Client A can send the key ID(s) to Client B using their normal connection link.
- Client B then gets the key(s) from the Phio TX Node it is assigned to using the key ID(s).
- At this point, both encryption devices have been supplied with the same symmetric key without using their normal connection link.
In this scenario, the key was never transmitted directly over the unsecure network that is the Internet, but only within the secure, redundancy and resilient Phio TX network (“hive”).
How Is Phio TX Deployed?
Phio TX can be deployed on-premises, in the cloud, or both as a hybrid deployment. For on-premises deployment, it is available as a FIPS 140-2 &3 validated, physical hardware appliance (with QRNG) or a virtual machine; for cloud deployment, virtual machines are hosted as an AWS cloud instance.
All nodes can incorporate with QKD systems and use PQC algorithms to secure their communications; the hardware appliance can optionally integrate a QNRG chipset to generate its own quantum entropy, that can be distributed to all the other nodes in the mesh network, referred to as the “hive.”
Depending on how their own infrastructure is organized, either they have remote offices in other regions or countries, the type of devices used by their employees (desktop or mobile), either they have QKD systems in place, customer can decide which version(s) of Phio TX to deploy, how many and where, even combining on-premises appliances with cloud-based ones to build a hybrid infrastructure, thus enhancing their security by delivering keys used to encrypt data between enterprise and cloud environments with the strongest security available.
Which PQC KEM Algorithms Does It Support?
Phio TX incorporates a large number of NIST PQC Key Encapsulation Method (KEM) candidates, including CRYSTALS-Kyber and Classic McEliece, that can be used to encrypt data inside a traditional TLS connection, effectively providing double encryption for the key distribution process between peer Phio TX nodes. This approach protects against quantum attacks while maintaining FIPS 140-2/3 regulatory compliance until a final PQC standard is adopted.
How Does Quantum Entropy Work?
Phio TX can use Quantum Random Number Generator (QRNG), Quantum Key Distribution (QKD), or FIPS-certified Cryptographic Pseudorandom Number Generator (CPRNG) as possible sources of entropy.
A physical Phio TX enterprise appliance, with built-in QRNG chip, can generate quantum entropy; also, if connected to a QKD system, Phio TX nodes will constantly request keys and unused ones are recycled into an entropy pool. Key material from both QRNG and QKD entropy sources is divided among all other Phio TX nodes in the hive. It is recommended to have at least one Phio TX with QRNG to provide quantum entropy to the Phio TX virtual/cloud nodes.
How Does Key Generation Work?
The key is generated upon request from the Client using FIPS-certified CPRNG. If the QRNG/QKD entropy pool is available, it is mixed with the other entropy sources. The resulting key has the property of being truly random satisfying FIPS certification requirements.
How Does Key Distribution Work Internally?
Each Phio TX node is configured to only accept connections from its designated, trusted peers. They communicate using a secure TLS connection, after mutually authenticating using PKI-based client-server and server-client certificate check; a PQC KEM algorithm, like CRYSTALS-Kyber, can also be enabled to provide double encryption with AES-encrypted tunnel within TLS. Additionally, if connected to a QKD system, QKD-derived keys are also used to encrypt data transmissions between nodes.
Also, the ability to use and send more than one key, thanks to the different paths available, allows key mixing, a unique feature that brings additional security; those keys are mixed by the endpoints so that only they know what the final encryption key is.
Which Protocols Are Used by the Clients to Request Keys?
Two protocols are available for client, called encryptors, to request key generation and distribution:
- ETSI GS QKD 014 Rest-based delivery API, developed by the European Telecommunications Standards Institute (ETSI), to become the standard protocol for QKD.
- Cisco Secure Key Integration Protocol (SKIP) proprietary protocol, soon available on Cisco ASR/ASA network appliances.
What About Mobile Devices?
But Phio TX is not limited to static systems (e.g., VPN access points, firewall), as Phio TX Mobile™ (TXM), developed by ISEC7 Software Ltd., extends that security to all endpoints, including mobile devices. It consists of a middleware mobile application available for iOS and Android devices that interfaces between a client application (e.g., a VPN client) and the Phio TX infrastructure; Phio TXM will securely request and retrieve the encryption key from the network for the client application on its behalf, using either standard ETSI or Cisco SKIP protocols, without the client application vendor having to redesign/redevelop its own application completely, allowing seamless integration. And this is possible from anywhere, in a quantum-secure way. Phio TXM application can also be configured and deployed remotely on employee’s mobile devices using a Unified Endpoint Management (UEM) solution.
The team at ISEC7 has been at the mobility security forefront for decades, working with companies in the private and public sectors to ensure their ecosystems are protected and their security posture endures through training and best practices. If there are any questions about Quantum Xchange’s Phio TX and/or how your current solution can be leveraged better, please reach out to the team at ISEC7 and we can complete a security assessment to help you navigate the options available to you to help strengthen and protect your infrastructure.
Contact
(C) Rémi Frédéric Keusseyan, Global Head of Training, ISEC7 Group












