
What is Single Sign-On?
Whenever we access public or corporate resources and services, we are asked to authenticate.
To ease that process and strengthen security, users are prompted to authenticate against a unique Identity Provider (IdP), using their work credentials (usually their email address) that will then allow them to access many websites and services, either on-premises or cloud-based, without having to re-authenticate again. This authentication mechanism is referred to as Single Sign-On (SSO).
The login window typically looks like a pop-up web window, as pictured below.
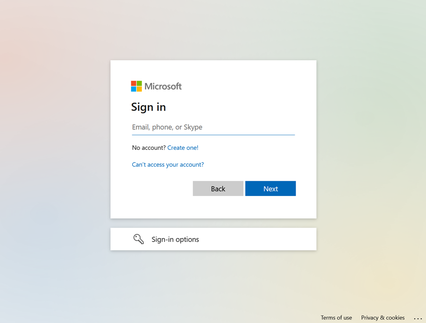
At this point, anyone would take for granted that this login banner is legitimate from a known, trusted vendor or party (in this case, Microsoft), and would enter their credentials without thinking twice. And that’s where Browser in the Browser (BITB) attacks come into play.
How Does BITB Work?
A BITB attack is an advanced, curated phishing attack that takes advantage of the SSO authentication mechanism to try to spoof a legitimate domain. It will replicate the entire process to create a fabricated browser window that aims to deceive users into believing they are authenticating against a legitimate Identity Provider (e.g., Microsoft), while they are in fact providing their credentials to a malicious party. What makes it so critical is that it is almost undetectable to the naked eye.
Let’s say an employee is trying to connect to an external service (e.g., online LMS) which is integrated with the company Identity Provider (e.g., Google) using Single Sign-On, so employees don’t have to create yet another account and password that they would need to remember and instead just use their everyday corporate account; if already logged into other corporate services within their browser, they might not even be prompted for their credentials again. So far, so good.
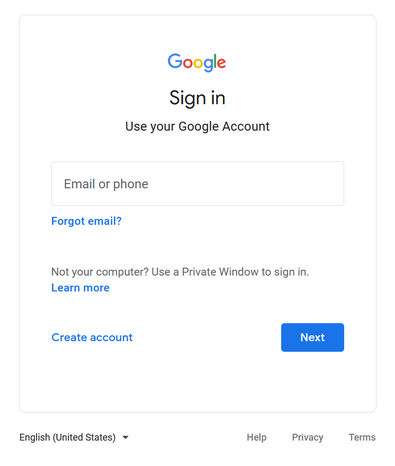
However, if accessing a spoofing domain, they might get a login window similar to the Google login window they are used to, and instead of sending their credentials, when prompted, to their trusted provider for validation, they send them out to a malicious third-party that would re-use them later to access their account and eventually steal their data.
Note that it might be easier to confuse with some Identity Provider (e.g., Google) unlike others, as some are used for both private (e.g., Gmail account) and work purposes (e.g., Google Workspace account), whereas other providers are mainly only used to access work-related services.
How to Protect Your Organization
The quick answer would be to stop using Single Sign-On (SSO), however in practice that might be quite complicated as it would not make users’ work life any easier, having to carry different pairs of credentials to authenticate against any on-premises or cloud-based services they need to connect to. This would be counter-productive, as they would end up not using those services anymore or use the same, simple password for every single account they have, greatly impacting the overall security of the company.
If not enabled yet, make sure your SSO process is paired with an additional authentication mechanism, like Multi-Factor Authentication (MFA). Though in theory it could still be bypassed by hackers (e.g., using malware), it is very unlikely and would help users avoid most if not all attacks, just like adding another lock to your door; a skilled, motivated thief would still be able to break in, but may very well give up or choose an easier target instead.
On top of that, having a Password Manager solution in place will further help detect illegitimate prompts. Since the phishing webpage is not actually a real browser window and the URL provided is not consistent with the one registered for the service the user is supposedly accessing, the autocomplete option will not be triggered, and thus credentials will not be provided to the illegitimate website.
Educate Your Employees
Ultimately, your employees are your first and last line of defense when it comes to phishing attacks.
They must be educated and trained properly on cybersecurity awareness, so they are able to spot, or at least be suspicious and double-check, whenever they get an unusual email, SMS, or suspicious pop-up login banner asking to provide their credentials.
Teach both your technical staff and employees on the specifics on those new attacks, which known, basic checks they can perform to confirm or discard whenever a potentially suspicious logon banner pops up on their computer. In any case, when in doubt, employees should immediately report to the IT security department. Better safe than sorry!
Now that you are aware of Browser in the Browser attacks, it is important to similarly educate your employees so they can recognize the hallmarks of a Browser in the Browser attack and avoid the devastating impact it could have on your ecosystem. Remember that educating your employees is one of the most important actions you can take, followed by pairing your Single Sign-On (SSO) process with an additional authentication mechanism like Multi-Factor Authentication (MFA) and using an enterprise password manager. The team at ISEC7 has been working with companies in the private and public sector to ensure their ecosystems are protected and that their security posture endures through training and best practices. Please reach out to the team at ISEC7, and we can complete a security assessment and help you navigate the options available to you to help strengthen and protect your infrastructure.
Contact
Source: http://bit.ly/bb-201016












