
In a previous article, we covered Mobile Threat Defense (MTD) solutions, offering threat detection, prevention, and response on mobile devices. Today we will cover similar functions but in more traditional desktop devices like workstations, laptops, and servers. Although the goal is similar, due to its own idiosyncrasies, the response is delivered in a different manner, with two different solutions providing a combined response: Endpoint Protection Platform (EPP) and Endpoint detection and Response (EDR).
What are Endpoint Protection Platform (EPP) and Endpoint Detection and Response (EDR)?
Endpoint Protection Platform (EPP) typically prevents file-based threats like viruses, malwares, and trojans alike from executing on an endpoint by identifying them using behavior-based security. Unlike traditional antivirus solutions, behavior-based security leverages the power of Artificial Intelligence (AI) and Machine Learning (ML), combined with the immense storage capacity of Data Lake (DL), to perform pattern recognition and discover any unexpected behavior that could potentially be a threat. Therefore, such solutions can also protect endpoints even if offline (no Internet connection) or not running the latest version, as they don’t look for file signatures, but suspicious behaviors.
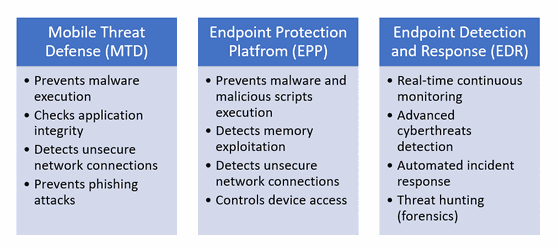
Endpoint Detection and Response (EDR), however, goes beyond this and detects more sophisticated attacks, for example, involving scripts or memory access. These will usually not trigger EPP detection as they are not technically malware but legit files (e.g., Word document), actions (e.g., run a script), and network requests (e.g., DNS request) that, when put together, would eventually represent a cybersecurity threat, for example, exfiltrating data from a computer to a back-end server on the Internet.
EPP on its own is good but not good enough, and it is recommended to use it in combination with an EDR solution to provide a more efficient floor-to-ceiling protection against cybersecurity threats, by proactively identifying potential cybersecurity threats and preventing them before they can unfold and spread over an infrastructure.
EDR does that by continuously monitoring all activities and collecting specifics on endpoints, including network requests (e.g., ARP, DNS, sockets, etc.), registry, memory dumps, and system calls. Once a possible attack or malicious data exfiltration attempt is detected, immediate action will be triggered based on predefined or customized responses. Additionally, with EDR you can perform a post-incident forensics investigation, usually referred to as “threat hunting,” to understand what happened, how the attack unfolded, and steps to take to protect your environment from such an attack occurring again.
In today’s ever connected world, all our devices will need to be protected. At the minimum, some kind of threat detection, prevention, and response solution is needed for all the applicable devices that access your corporate data. Those solutions should work in concert with the rest of your security apparatus to ensure your overall security posture is where it needs to be to protect your data and ultimately your liability. The team at ISEC7 has been working with companies in the private and public sector to ensure their ecosystems are protected and that their security posture endures through training and best practices. Please reach out to the team at ISEC7, and we can complete a security assessment and help you navigate the options available to you to help strengthen and protect your infrastructure.
Contact
(C) Rémi Frédéric Keusseyan, Global Head of Training, ISEC7 Group












