Organizations want to secure corporate data without having to compromise user experience and the latest iOS and iPadOS releases have great device management capabilities that embed security and user privacy.
I’m excited to share that MobileIron offers day zero compatibility and key feature support across its product portfolio for the following iOS 14 features:
Wi-Fi Mac Address Randomization:
A new critical privacy feature introduced by iOS 14 is Wi-Fi MAC Address randomization. With iOS 14, whenever a device is associated with a Wi-Fi network, it will use a random MAC address instead of the device's true hardware MAC address and the challenge for admins is that they may not be able to associate this MAC address to a specific device. In order to ensure device/user compliance with corporate and regulatory policies, and ability to monitor end user activity, admins can disable the Wi-Fi Mac address randomization setting in MobileIron admin console. MobileIron made this new setting available to customers on day zero.
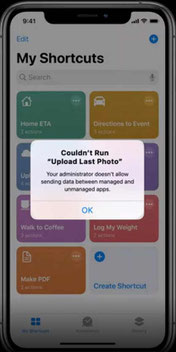
Managed Open in supports Shortcuts:
iOS 14 brings in a new feature that will control proprietary data flow using the productivity app called Shortcuts. With shortcuts supported by Managed Open In, admins have the ability to prevent the flow of sensitive enterprise data to unmanaged apps and services. Having the Managed Open In settings already available with MobileIron, customers can take advantage of this feature from day zero of iOS14 release.
eSIM Identifier:
Apart from the above feature support, MobileIron is also working actively to make other new iOS14 features such as Non Removable Managed Apps, Managed Notifications Preview, Set Time Zone available in our upcoming releases so customers can take advantage of the new capabilities.
At MobileIron, we are committed to providing excellent customer service and support. We look forward to helping our customers leverage the powerful updates in iOS 14.
Statements in the blog concerning future product availability and plans are forward looking statements, and they are subject to change. They do not represent a commitment, promise or legal obligation to deliver any material, code or functionality, and should not be relied upon in making purchasing decisions.
3) How can an enterprise security team best protect against mobile threats?
First, you should map out your attack surface and identify the mobile threats you are most exposed to, focusing on any unmitigated risks before choosing a vendor with the expertise that matches your need. The point here is to think like an attacker: Ask yourself whether you have employees with jailbroken devices, vulnerable software, or sensitive data that might be traveling through unencrypted channels. Perform a detailed analysis of your attack surface and how data moves between your mobile and stationary environments. As I mentioned in my accompanying video, eliminating any trust assumptions here is critical for a Zero Trust security posture. Wherever access to sensitive data is permitted, there should be access controls in place and appropriate isolation based on real-time risk. Also, consider whether a lack of device-level security is putting you at a greater risk for software exploitation. Mobile technology vendors are constantly improving their operating systems’ native anti-exploit capabilities as they roll out new versions and updates; keeping this software up-to-date should be a priority.
As you begin to rely more on native OS-level security features for device-level security, you can focus more on what matters the most: protecting the apps and your corporate data. You should have app management in place with jailbreak detection and data isolation using technologies like app containerization or virtualization. Browser protection should include malicious URL protection. Overall, the more management you can do in the app layer, the better. This will allow you to decouple protection from the devices and infrastructure and focus on protecting your sensitive data and apps consistently across all device types, regardless of device posture or ownership. Ultimately, it would help if you strived to protect every device with access to corporate resources against threats like phishing and sensitive data theft.