There are many enterprise and consumer applications outside of the Mac App Store and it has become an accepted workflow to search for an application on the internet and then install it using an installer downloaded from the internet.
To summarize how the Mac malware works:
- A user downloads an application (file) installer from the internet by searching for a software.
- Native Apple features (more on this below) block the app from being installed.
- The malware developer provides user guidelines on how to circumvent security controls and install the app.
- The intended software is now installed by the downloaded malware package, including the hidden malware payload
Any Mac user could fall victim to this eloquently presented trick and install malicious software. After all, following instructions and guidelines to circumvent built-in security controls has been a mandatory task to install certain known good software in the past.
The norm of downloading and installing applications from the internet is extremely troubling for enterprises, but with MobileIron’s Mac management capabilities, admins can choose to completely block this behavior. You can completely block all apps that are downloaded from outside the Mac App Store.
My recommendation to many customers is to block everything and then create a list of a select few applications that you want to allow in your enterprise. That is, if you really want to allow something through the gates. Apple calls this feature Gatekeeper for a reason!
The gates, or what Apple calls Gatekeeper, enforces code signing and verifies downloaded applications before allowing them to run, thereby reducing the likelihood of accidentally executing malware. The Gatekeeper settings and behavior can be configured through MobileIron’s unified endpoint management (UEM) solution.
In the case of an enterprise managed Mac, you can configure the Gatekeeper to have the following behavior:
- Apps from MDM server are allowed.
- Apps from Mac App Store are allowed.
- Apps from anywhere else are blocked.
- And lastly, if (and it’s a BIG if) you create a rule to allow specific apps (which are not from either the Mac App Store or from MDM), you can specifically define rules to do so.
Here are the MobileIron steps to configure the Gatekeeper to have the behavior for points one to three listed above:
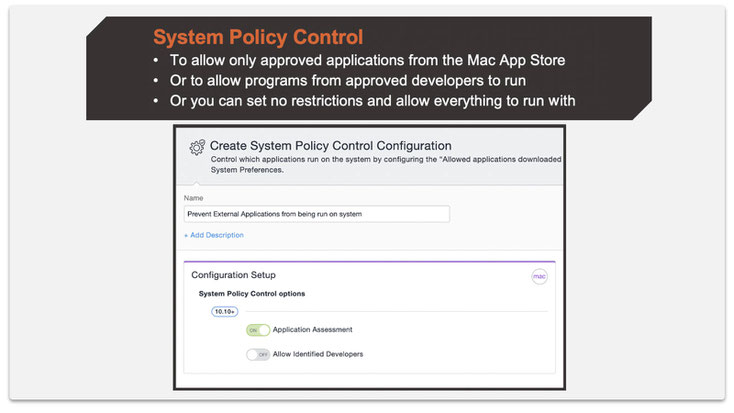
Step 1: Create a System Policy Control configuration.
The below setting only allows applications from the Mac App Store.
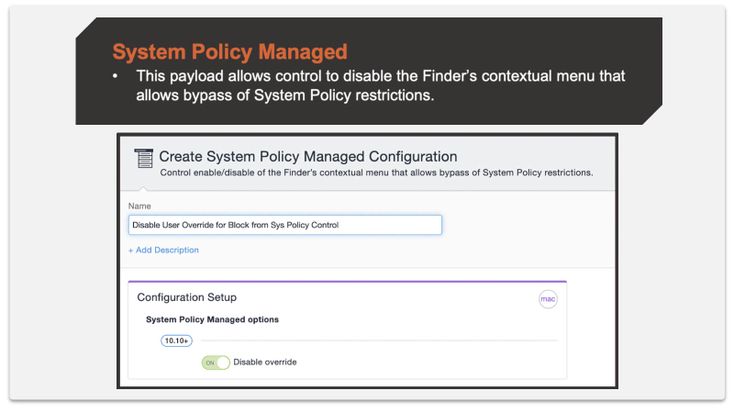
Step 2: Create a System Policy Managed configuration.
The below setting disables users the option to override the block.
That’s it! Now, if you want to selectively allow something through the Gatekeeper that is from the internet, you can create an additional sophisticated rule.
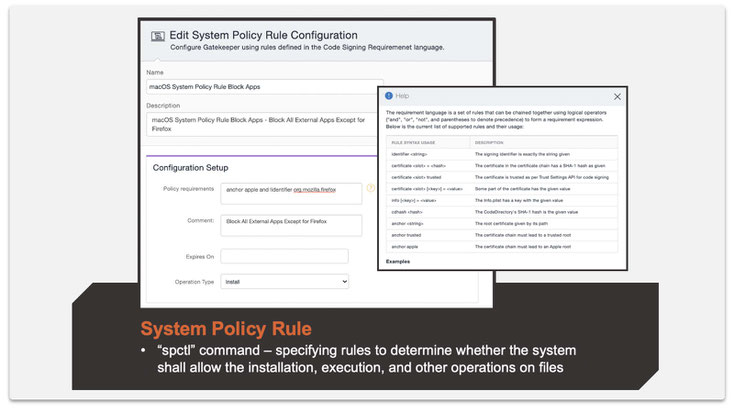
Step 3: Create a System Policy Rule configuration.
The below setting is shown for Firefox, but you can be creative and make it work for more applications. Also, the rules you can use can get very granular.
The above are preventative mechanisms specifically for enterprise Macs under management by a UEM solution. While these controls cannot be applied to a personal Mac in a MDM-less scenario, Apple still hasn't forgotten about its core security focus. Apple has been hard at work to make Macs the most secure hardware and software platform available. I have highlighted some of their recent security controls below:
- Hardware Security through the T2 chip. This is the next generation of hardware security. MDM is the only choice when it comes to management of these devices.
- Safely run apps - App Notarization (more below) and Privacy Preferences. An old blog here takes you through Privacy Preferences.
- Regular OS updates - Apple helps organizations keep their iOS, iPadOS and macOS devices secure with software updates. MobileIron can help here as well, with either ensuring faster upgrades or giving you time (up to 90 days) to defer an upgrade.
-
System Integrity Protection, commonly known as SIP, ensures the OS remains tamper-proof
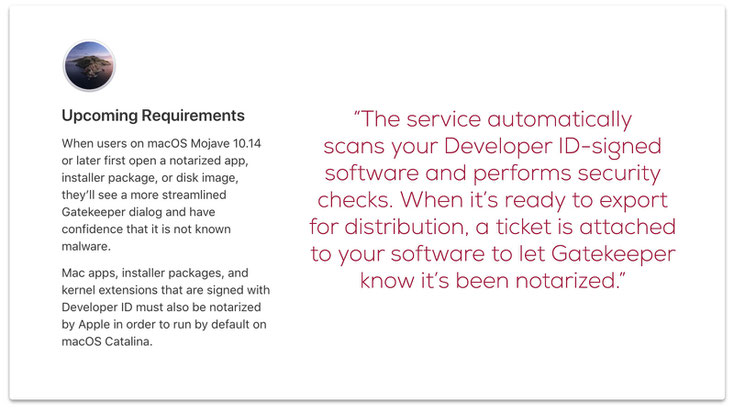
App Notarization: Now, what is that?
There is an option to allow apps from “Apple Identified Developers” to be allowed through the Gatekeeper. As you can see in the first screenshot above, we turned it off in our recommendation. Here is why:
It could be possible for someone to sign up as a developer with Apple and then create malware, host it some place, pay for Google Ads, and wait for the sun to shine. And users could download the malware before Apple finds out and revokes his or her developer certificate and adds him or her to the list of signatures that Gatekeeper should block.
But with App Notarization, it is mandatory for a developer who chooses to keep apps outside the Mac App Store to get a stamp of approval (notarization) from Apple by submitting the apps to Apple and passing through the safety check.
As per Apple:
Any app that does not have a notarization stamp, in addition to the existing requirement of being an Apple Identified Developer, would be blocked by Gatekeeper.
Summary
Apple provides many security features in its devices. Many times, it is upon the user to adhere to these. By bypassing these security measures, users may risk corporate security unknowingly. It is on IT to keep such use cases in mind if security is of grave concern to the organization. By using MobileIron, admins get tools to work with OS security features and ensure a smooth user experience complementing Apple’s user experience and security. To see this in action, check this video.
-------
Scource: MobileIron.com