
You hear it in the news. Your colleagues chat about it on the
elevator. It sounds problematic. It is. Baltimore’s budget office estimates a ransomware attack on city computers will cost at least $18.2 million (Baltimore Sun). There have been 22 known
public sector attacks so far in 2019 (CNN).
Hackers are working every minute to break into systems, take valuable and personal information, and sell it on the dark web or hold data for ransom. Maybe you haven’t personally experienced the violation or your finances or your company hasn’t been pegged with a breach. But the truth is, you just might not know it yet. I don’t know about you, but I find stats, like the ones published by Cisco and Cybersecurity Ventures, unsettling. Their report includes the following:
- Ransomware attacks saw a 350 percent increase in 2018, according to one estimate. Cybersecurity Ventures expects that businesses will fall victim to a ransomware attack every 11 seconds by 2021, up from every 14 seconds in 2019, and every 40 seconds in 2016.
- Cybercrimes are vastly undercounted because they aren’t reported — due to embarrassment, fear of reputational harm, and the notion that law enforcement can’t help (amongst other reasons). The unit chief at the FBI’s Internet Crime Complaint Center (IC3) stated that the number of reported cybercrimes in the agency’s reports only represent 10 to 12 percent of the total number actually committed in the U.S. each year.
- The 10 biggest data breaches of all time — with the number of accounts hacked and year occurred — according to Quartz: Yahoo, 3 billion (2013); Marriott, 500 million (2014-2018); Adult FriendFinder, 412 million (2016); MySpace, 360 million (2016); Under Armor, 150 million (2018); Equifax, 145.5 million (2017); eBay, 145 million (2014); Target, 110 million (2013); Heartland Payment Systems, 100+ million (2018); LinkedIn, 100 million (2012); rest of list.
- The FBI reported that the Business Email Compromise (BEC), aka Email Account Compromise (EAC) — a sophisticated scam targeting both businesses and individuals performing wire transfer payments — has cost more than $12.5 billion in losses over the past 4.5 years (as of its last tally through May 2018).
Meanwhile, we are all embracing a mobile world. People want the benefits of technology, time-savors, mobile access to information and mobile applications, ways to connect easily with other people and communicate on-the-go. We are all getting numb to privacy and freely giving up our personal information, too – all for convenience or a fun mobile game that may give us animal ears in our photos.
There are 4 billion internet users worldwide, and that number is growing. It is a hackers dream. As more people open their personal lives up to hacker access, the opportunity sharply widens for access to government and commercial workplaces.
Securing data use to be simpler. Physical perimeters kept data inside the walls of the physical workplace. But now the workplace is everywhere outside the physical workplace, and the workforce is walking around every corner of the world with mobile devices, they greatest vulnerabilities.
Most cybercrime is now mobile. Over 60% of online fraud is accomplished through mobile platforms. Additionally, 80 percent of mobile fraud is carried out through mobile apps instead of mobile web browsers, according to RSA.
Do you have a music or Kindle or exercise app on your phone? And do you have work information on your
phone? Most people do. It only takes one worker and a mobile device to open access to workplace data.
Our state and local governments and cities are high targets crippling operations putting cities in a standstill. Performing daily responsibilities and protecting field employees is strained. It is no longer just on the news where you can turn the channel. It is in our back yard. While we face current emergency incidents, we can still run parallel efforts to build a new strategy for workforce
mobilization.
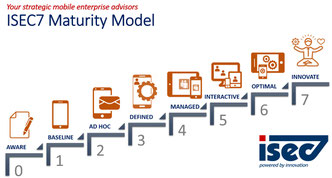
Not sure where to start? There are many great vendors for mobile solutions, mobile device management, and mobile threat detection. The strategic mobile advisors at ISEC7 can help navigate the mobility industry, the semantics and assist with vendor selection to meet your agency requirements. We will also asses your existing legacy systems and help to repurpose your architecture while building a roadmap for mobile modernization.
The answers to hard questions around data protection starts with prioritizing a new approach to data management. Begin work focused on the greatest vulnerabilities, mobile endpoint access. It sounds serious. It is. Consider more information about ISEC7’s Mobile Enterprise Maturity Model. To speak with a mobile expert, email us at info@isec7.com.












